Overview
Users frequently connect to hotspots to enjoy free-of-cost service (as opposed to mobile data connections). A hotspot may have a captive portal, which usually consists of a web-page that allows users to choose their preferred language and confirm acceptance for the terms of service. The captive portal is used to communicate hotspot privacy policies, collect personal identification information such as name and email for future communications, and authenticate guests if needed (e.g., by asking the user to login to their social media sites). Then, if the user accepts the hotspot's policies, she is connected to the internet and her web browser is automatically directed to load a landing page (usually the service provider's webpage). We analyze tracking behaviors and privacy leakage for the following hotspots.
Analyzed hotspots
 |
Gymnasium |
 |
Bank |
 |
Telecom Kiosk |
 |
Transportation |
 |
Shopping mall |
 |
Hotel |
 |
Cafe and Restaurant |
 |
Retail Business |
 |
Art and Entertainment |
 |
Library |
 |
Hospital |
 |
Car Rental |
Summary of Findings
Hotspots Scorecards
Click here for information about the evaluation ciriteria .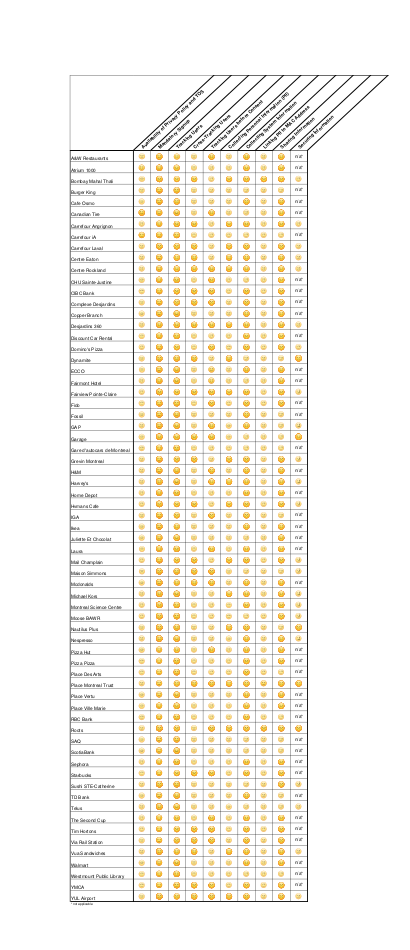
Personal information collected by captive portals via social login, direct registration, or surveys
27 hotspots use social login (Facebook, LinkedIn, Google, Instagram) or a registration page to collect significant amount of personal information (19 hotspots make this process mandatory). Several hotspots also collect personal information via a separate survey page. Social login providers can expose several privacy-sensitive PII items--e.g., we found that LinkedIn shares a user's full name, email address, profile picture, current employment, and basic profile with some hotspots.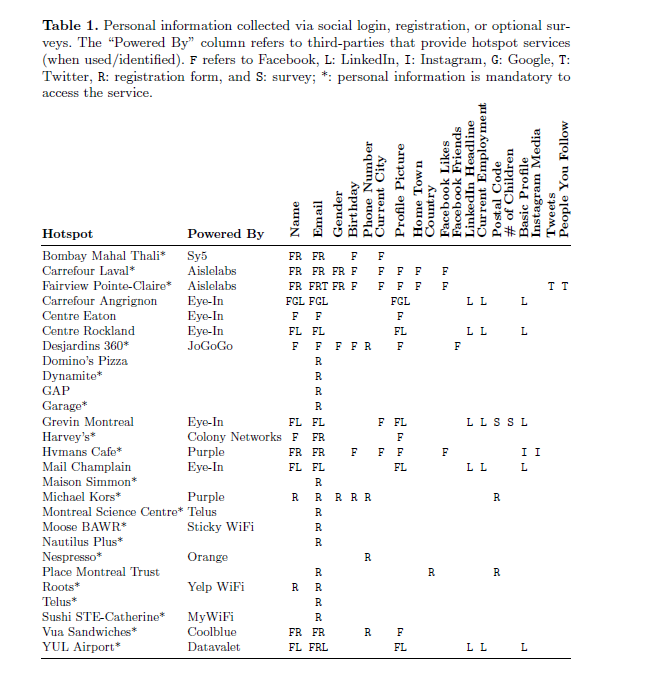
Number of third-parties in captive portals
Except three, all hotspots use tracking technologies on their captive portals and landing pages. On average, we found 7.4 third-party tracking domains on each captive portal (max: 34 domains, including 7 known trackers). We accumulate the distinct trackers as observed in all the datasets collected for a given hotspot.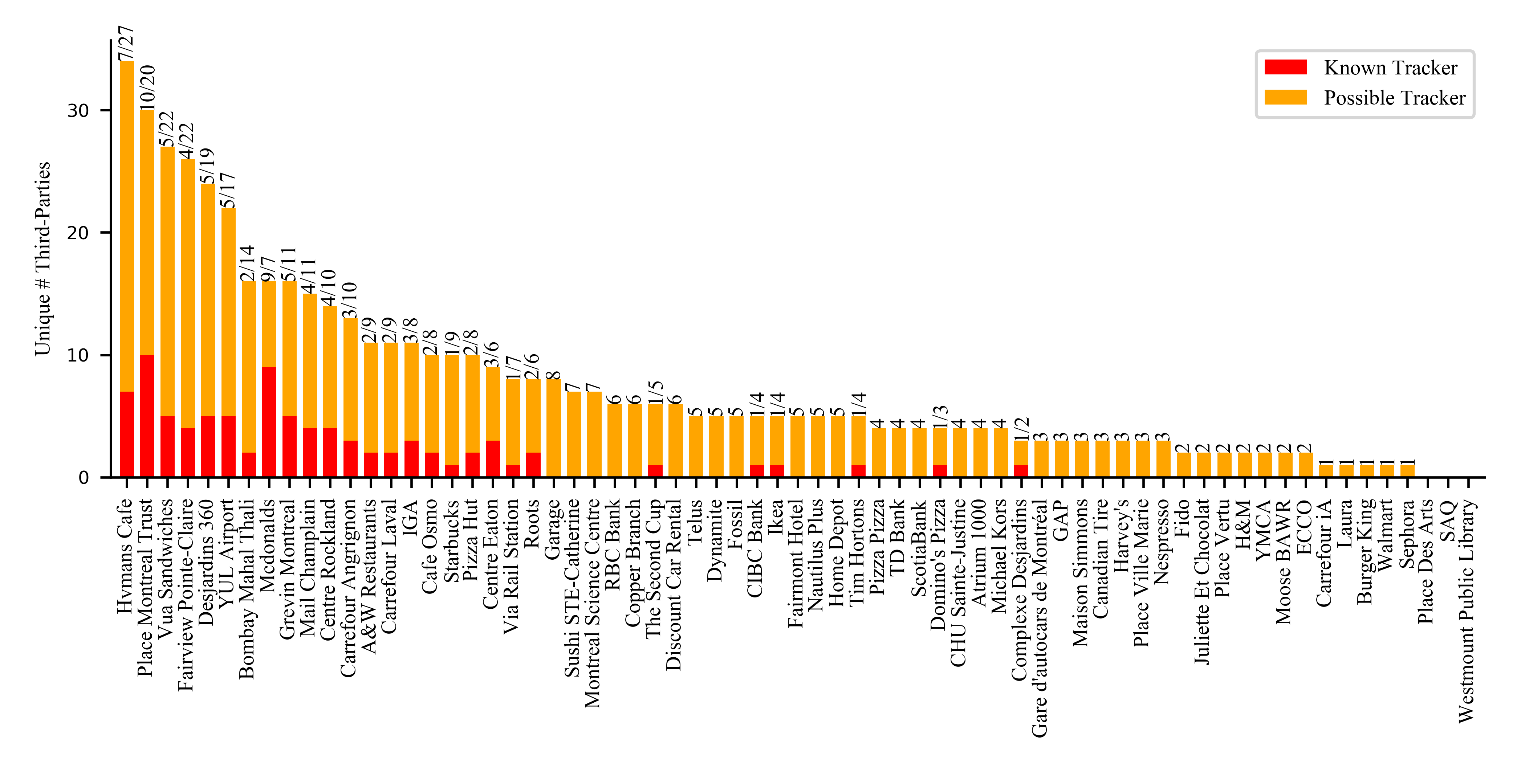
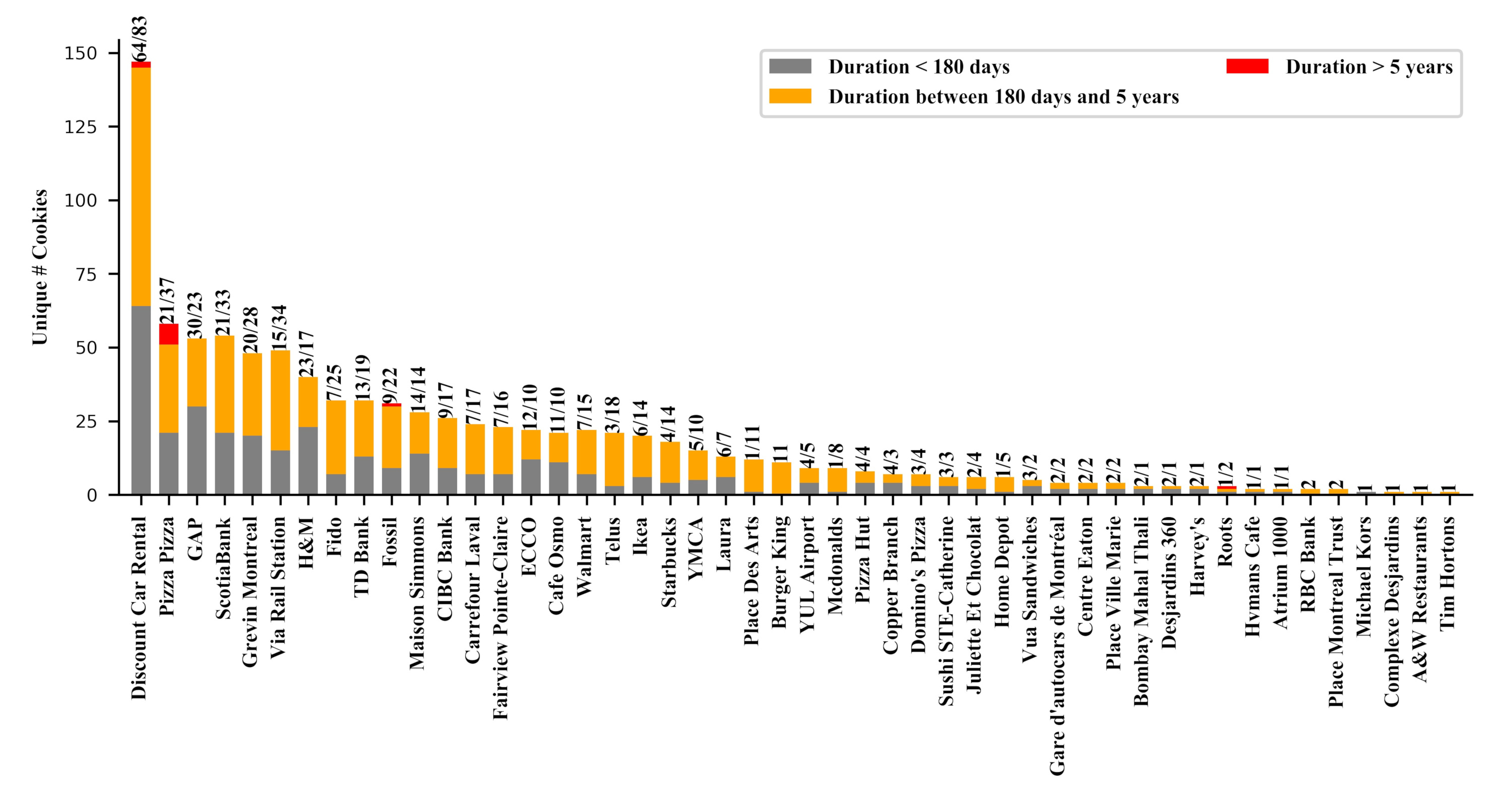
Number of third-party cookies in captive portals
40 (59.7%) hotspots create third-party cookies valid for various duration|e.g., over 5 years from 10 (14.9%) hotspots, six months to five years from 23 (34.3%) hotspots, and under six months from 38 (56.7%) hotspots. Surprisingly, 26 hotspots (38.8%) create persistent cookies even getting explicit user consent on their privacy/terms-of-use document.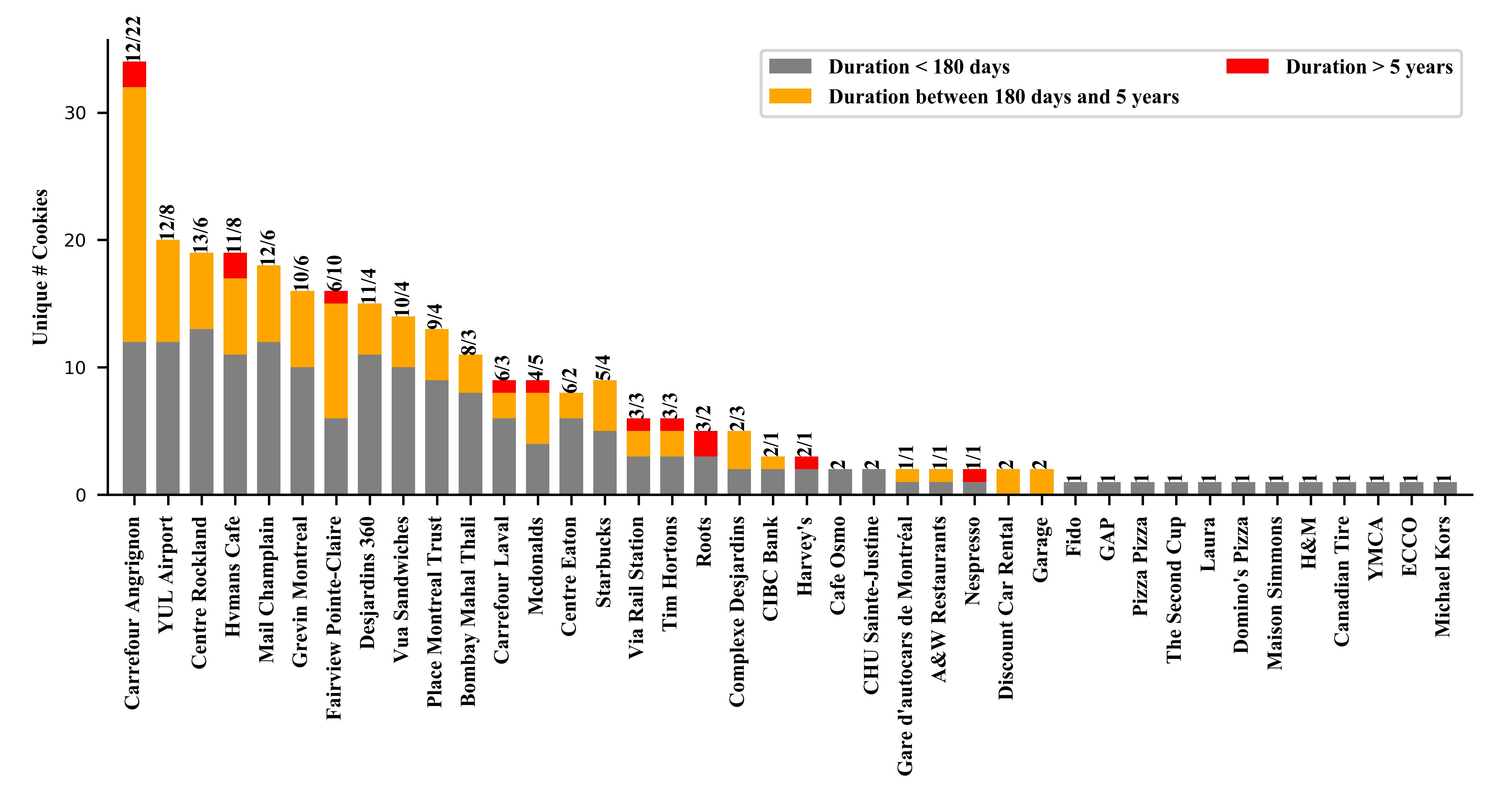
Number of third-party cookies in landing pages
We found 48 (71.6%) hotspots create third-party cookies valid for various durations|e.g., over 5 years from 4 (6.0%) hotspots, six months to five years from 47 (70.1%) hotspots, and under six months from 42 (62.7%) hotspots (with max validity of 99 years).